Conficker Continues
The BBC has an article on Conficker, the virus that everyone seemed to think passed us by on April 1st.
The Conficker worm has started to update infected machines with a mystery package of data.
Computer security firms watching the malicious program noticed that it sprang into life late on 8 April.
The activity on its update system delivered encrypted software to compromised machines. It is not yet clear what the payload contains.
The Conficker virus variants are thought to be present on millions of PCs around the world.
Spam connection
The updating activity has begun about a week later than expected. Analysis of the “C” variant of Conficker (aka Downadup) revealed that its updating mechanism was due to go live on 1 April.
The belated updates were spotted by researchers for Trend Micro following the arrival of a new file in one of the directories in so-called “honeypot” machines deliberately seeded with Conficker C.
Analysis showed that the file had arrived via the peer-to-peer file transfer system that infected machines use to communicate.
In a bid to avoid alerting people to its activity, the update is slowly being trickled across the population of machines harbouring the C variant. Exact figures for the number of Conficker-infected machines are hard to determine, but the minimum is widely believed to be three million.
“The Conficker/Downad P2P communications is now running in full swing,” wrote Ivan Macalintal from Trend Research on the company’s security blog.
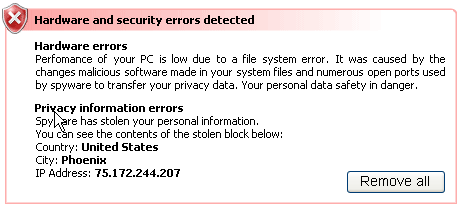
Once it arrives on a machine, the package of data randomly checks one of five different websites – MySpace, MSN, eBay, CNN and AOL – to ensure its host still has net access and to confirm the current time and date.
Following this check the data package removes all traces of its installation.
The strong encryption on the payload has, so far, prevented detailed analysis of what it actually does. However, security experts speculate that it is a “rootkit” that will bury itself deep in Windows in order to steal saleable data such as bank website login details.
Security researchers are continuing to analyse the payload to get a better idea of what it is intended to do.
Symantec said it too had noticed the increased activity of Conficker and its analysis suggested a link with another well-known virus called Waledac. This malicious program steals sensitive data, turns PCs into spam relays and opens up a backdoor so the machine can be controlled remotely.
The security firm noticed that the update also included an instruction to the worm to remove itself on 3 May, 2009. However, the Waledac imposed backdoor on the machine will remain open, so its creators can still control compromised PCs.

 SUPERAntiSpyware
SUPERAntiSpyware Download the Malicious Software Removal Tool
Download the Malicious Software Removal Tool