As of iTunes 9, it is pretty simple to move the iTunes library from one computer to another, even between Windows and Macs. These instructions detail a move from a PC to a Mac.
- Update to latest version of iTunes on both systems. In Windows: open iTunes, then Help -> Check For Updates. On Mac: open System Preferences then Software Update.
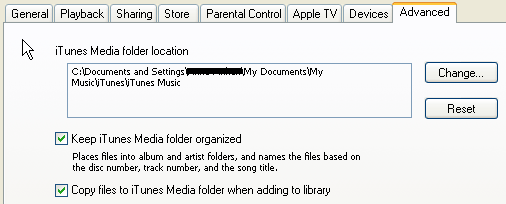
- In Windows: open iTunes’ preferences (Edit -> Preferences) and click the Advanced tab. Check both Keep iTunes Media folder organized and Copy files to iTunes Media folder when adding to library. These settings keep all your media files in the main iTunes Media folder, which you will later copy to your Mac.
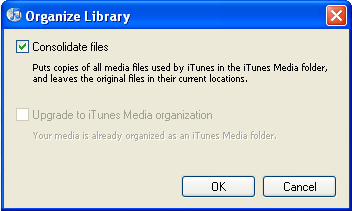
- In Windows iTunes: Choose File -> Library -> Organize Library. Check Consolidate Files, then click OK. This moves any files that weren’t in the right folder and makes sure that the library file has the correct pointers to these files’ locations. If the Upgrade To iTunes Media Organization option is not dimmed, check this too; it sorts your files in separate sub-folders.
- Copy the iTunes folder (in Windows 7 located in username\My Music\iTunes, in Windows XP located in Documents and Settings\username\My Documents\My Music\iTunes). You can copy by sharing the folder over the network, copying the folder to an external drive, or by pulling the Windows computer’s hard drive and attaching it to the Mac by a USB adapter (see picture). Pulling the drive is usually the fastest method if you have a huge library. Copy the iTunes folder to the Music folder in your user folder on the Mac. If there is already an iTunes folder, it means you’ve launched iTunes at least once on the Mac. If there’s no music there, you can just replace the folder. However, if you’ve already added music, you won’t be able to merge the libraries; in the iTunes Media folder, found in the iTunes folder, move the Music folder to your desktop and add those files into iTunes after you’ve completed this process. (Note that you’ll lose any playlists and play counts associated with those files. Alternatively, you can add the music from the PC to Mac’s iTunes by dragging it into iTunes, thereby losing the playlists etc of the PC’s music.)



 Use a password manager. Seeing a theme here about the importance of passwords? If you have different random passwords and change them regularly, then you either have a memory like Rain Man or you keep track of the passwords somewhere. The most popular software tools to manage passwords are
Use a password manager. Seeing a theme here about the importance of passwords? If you have different random passwords and change them regularly, then you either have a memory like Rain Man or you keep track of the passwords somewhere. The most popular software tools to manage passwords are