Viruses Abound
Every week I remove viruses from Windows computers. Here’s a common scenario:
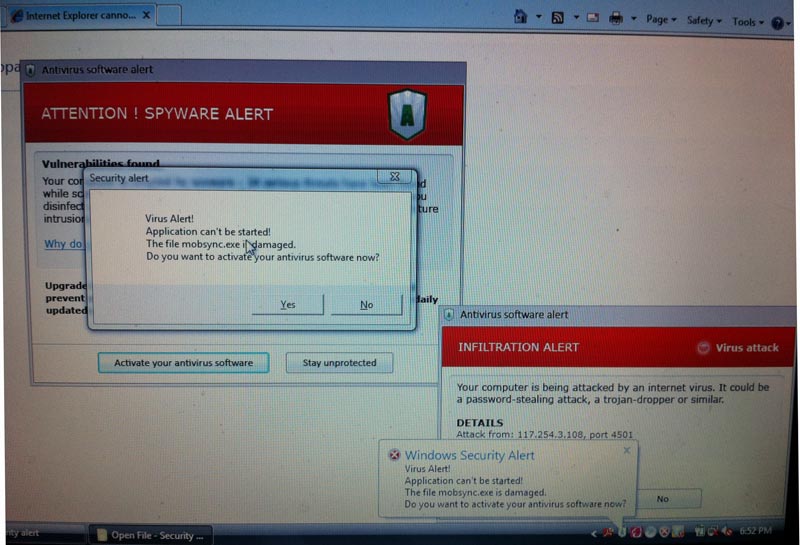
Someone gets a fake alert like this and realizes that they have a virus.
When they call me, I tell them to turn off the computer. This is because a virus can continue to inflict more damage. It can install other viruses and even encrypt your hard drive to hold your data hostage to demand a $200 ransom. Turning off a computer stops whatever the virus is doing.
Use a Live Rescue CD
The first thing I do with the computer is boot into a Live CD to search for viruses. Typically the computer displays the key to press for boot options. It is usually one of these: F1, F2, , F10, F12 or Del. The computers may be set up to boot from the CD if one is available.
By booting into another operating system, you keep the virus from running, inflicting damage, and actively thwarting virus scans. The Live CDs I use include:
Lately, I have found Kaspersky Rescue Disk to be the most effective. This approach also works from a USB stick if the computer’s BIOS supports booting from USB.
Update Virus Definitions
Because new viruses are out all the time, it’s best to update the virus definitions. This is done by connecting the computer to the Internet by an ethernet cable if your Live CD supports it.
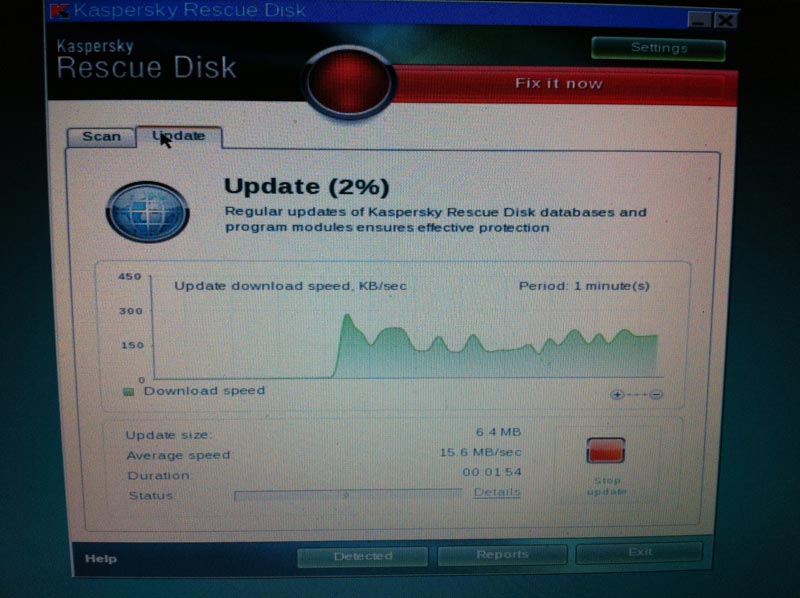
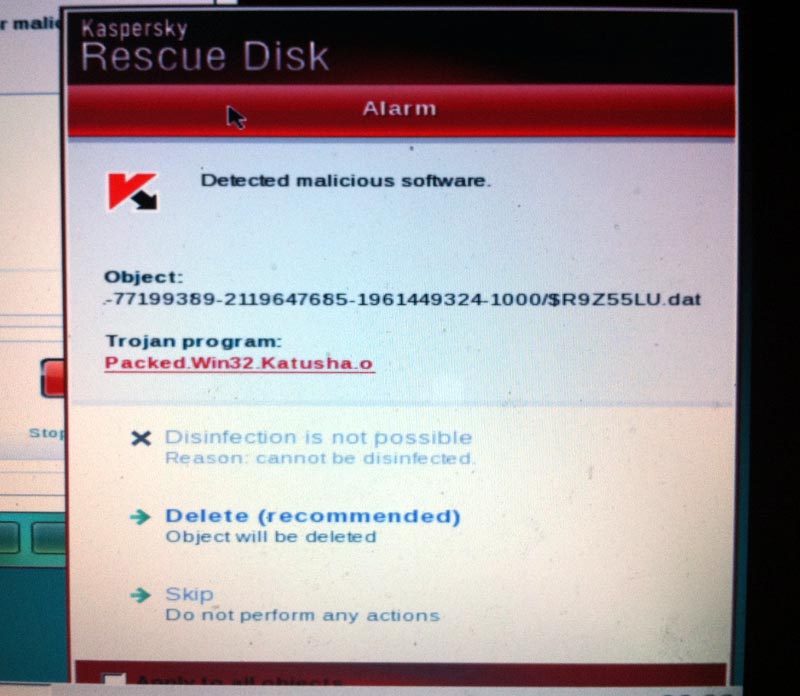
Scan for Viruses
Kaspersky typically finds viruses like this, a trojan named Packed.Win32.Katusha.o.
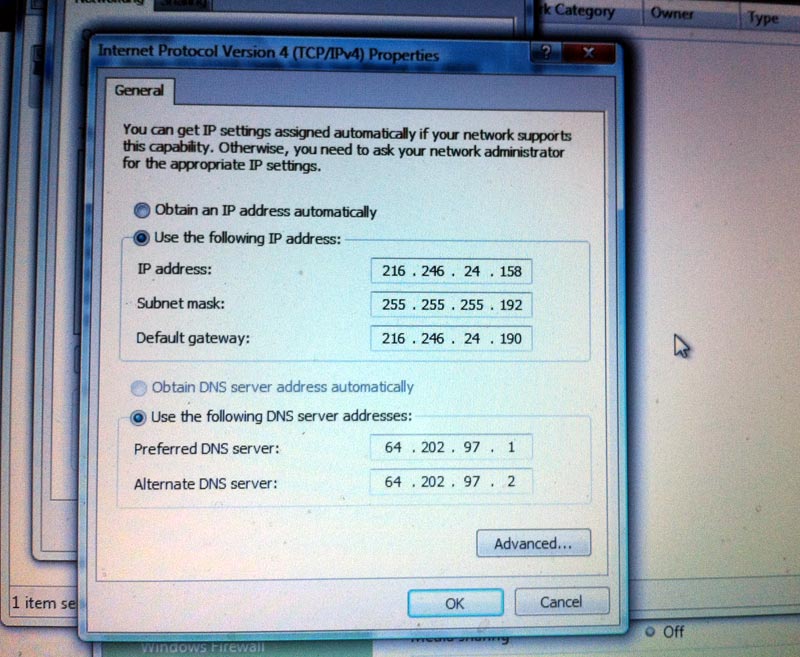
Boot Computer and Fix Internet Redirects
Boot the computer, then check for a Proxy setup in Internet Explorer’s Connection Settings. If there is one, disable it by changing to automatic settings. Similarly, check your network connection properties for IPv4 TCP/IP. Often you will see something like this, which should be changed to automatic settings.
Install Microsoft Security Essentials
There are a lot of decent Antivirus programs, but I like Microsoft Security Essentials because it finds viruses, is lightweight, and is free without nagware.
Other Things To Do
If there are still problems, other things that can be done:
- Install Malwarebytes Antimalware or other antivirus software if you still suspect problems. You should not typically run multiple antivirus programs at once.
- Boot into Safe Mode (F8 key at computer startup) to make system changes if you suspect that there is still an active virus. Or try another Live Rescue CD.
- Uninstall unused or virus-installed programs, available in Control Panel – Uninstall a Program.
- Remove startup items from Programs – Startup folder. You can also remove startup items by typing msconfig into the Start or Run box.
- Give up on system. Wipe the hard drive and reinstall the operating systems and programs. Sometimes this is the only remaining option if the operating system has been severely compromised. By pulling the drive and connecting to another computer as a peripheral drive, you can backup the data.
Run Windows Update
By running Windows Update and installing all the service packs, you are applying security patches and reducing the likelihood of getting viruses in the future.
Conclusion
Viruses can be scary and destroy your data. These steps can help, but once you have a virus, there are no guarantees. An infected computer is owned by the virus folks.
Therefore, in addition to protecting your computer, you should have backups of your important files such as photos or financial documents. If you have sensitive data, it can be encrypted with TrueCrypt or other tools.